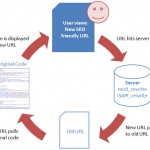
Cyber War between two countries Pakistan & India is again seems re-established. I remember one meeting between Pakistan Cyber Army & Indian Cyber Army where they commit to stop these attacks and utilize their skills for good.
There are many websites related to Pakistani & indian government were defaced by these two groups.
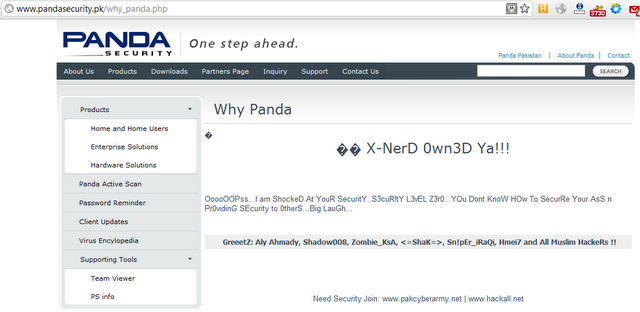
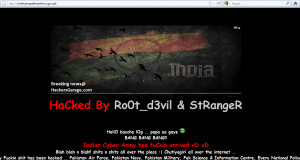
This time two people Ro0t_d3vil & StRangeR from ICA involved in defacement of Chief Minister Khyber PukhtunKhwa Official Goverment website
We tried to check the site security and it looks really funny.
HG Analysis :
- Google Index
- SQL Dorks found (May be RFI by ICA)
- Original Site (Google Cache) can be view here
That’s from us. Stay tune for more updates.