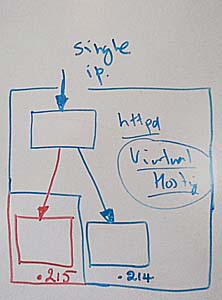
Scenario :
Our client required mod_proxy module for their application. Apache is already installed on WHM/CPanel CentOS Linux Server that run few websites. We thought recompiling Apache is not a good option that will require a down time for maintenance window and a small error can put our contract at risk and lost for our client.
What is ModProxy?
Mod_proxy is an Apache module that implements a proxy for your Apache web server. It is divided into further modules for different purposes. For example mod_proxy_http, mod_proxy_connect, mod_proxy_ftp, mod_proxy_ajp, mod_proxy_balancer. In our case we will compile few of them that are required for our application.
Installation :
Check Apache current version :
/usr/local/apache/bin/httpd -v
Output :
Server version: Apache/2.2.19 (Unix)
Server built: Jul 4 2011 06:24:27
Go to http://archive.apache.org/dist/httpd/ and pick your matched apache version. In our case it is Apache 2.2.19
cd /tmp/
wget http://archive.apache.org/dist/httpd/httpd-2.2.19.tar.bz2
tar -jxvf httpd-2.2.19.tar.bz2
cd httpd-2.2.19
./configure --enable-mods-shared="proxy proxy_http proxy_connect"
Note : You can add additional mod_proxy modules inside inverted commas. In our case "proxy proxy_http proxy_connect"
cd modules/proxy/
/usr/local/apache/bin/apxs -i -a -o mod_proxy.so -c mod_proxy.c proxy_util.c
/usr/local/apache/bin/apxs -i -a -o mod_proxy_http.so -c mod_proxy_http.c proxy_util.c
/usr/local/apache/bin/apxs -i -a -o mod_proxy_connect.so -c mod_proxy_connect.c proxy_util.c
/etc/init.d/httpd restart
Installation is completed.
You can verify modules under Apache modules directory.
ls -l /usr/local/apache/modules/mod_proxy*
Output :
/usr/local/apache/modules/mod_proxy_connect.so
/usr/local/apache/modules/mod_proxy_http.so
/usr/local/apache/modules/mod_proxy.so
If you have any question, feel free to comment below.